Ensuring strong IT security is crucial at a time when technology is at the forefront of business operations. Because of the complexity of contemporary IT infrastructures and the constantly changing nature of threats, protecting sensitive data and preserving operational integrity requires a multifaceted strategy. In this blog, we examine how businesses can strengthen their IT security posture by utilizing ITMS features.
Before understanding the ITMS in a detailed way let's try to understand what ITMS refers to
ITMS:
ITMS typically refers to “IT Management Suite” is a whole suite of software tools and solutions made to assist businesses in efficiently managing their IT infrastructure. These suites frequently come with a variety of features and modules that address various aspects of IT management, including patch management, asset management, software deployment, security, and more.
IT administrators and organizations frequently utilize ITMS solutions to automate and simplify processes linked to the management and security of their IT assets. With the use of these tools, one can increase total IT governance, decrease manual labor, and increase efficiency.
Let's see how can we enhance IT Security with ITMS:
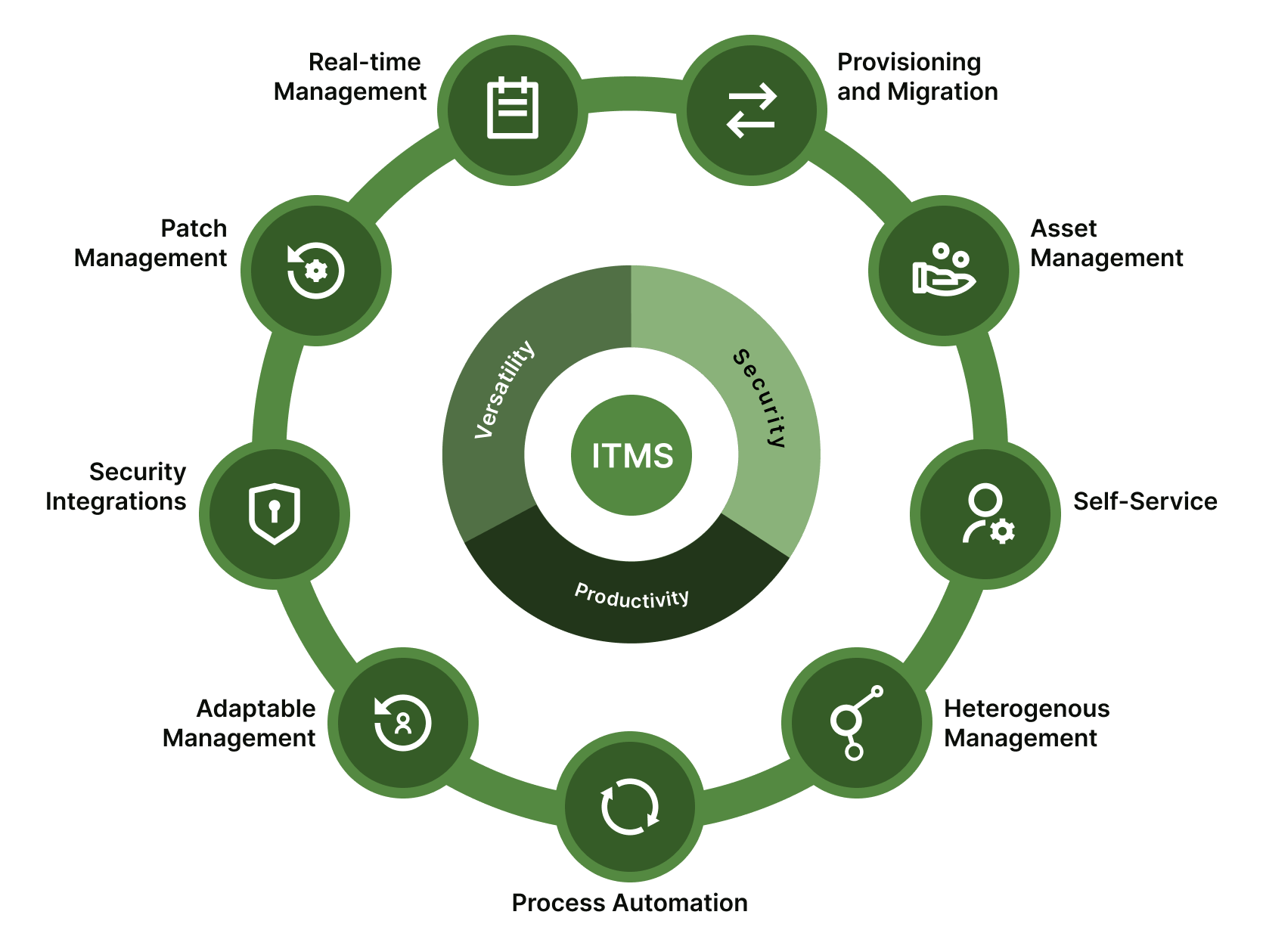
1) Asset Management:
Understanding and controlling the organization's digital assets is the first step in developing a strong IT security plan. ITMS offers inventory control and automated discovery tools, laying the groundwork for complete asset management. Organizations may discover potential vulnerabilities and make sure every device is accounted for by keeping an up-to-date inventory of hardware and software assets. This lays the foundation for successful security measures. After setting the foundation correctly it is important to fix the security patches
2) Bringing Excellence in Patch Management:
Keeping software and systems up-to-date with the latest security patches is crucial in mitigating potential vulnerabilities. Patch deployment throughout the company is streamlined by ITMS's automated patch management capabilities. Through regular vulnerability assessments, vulnerabilities are identified and prioritized, ensuring a proactive approach to cybersecurity while also lowering the chance of exploitation.
3) Centralized Software Deployment:
ITMS gives businesses the ability to centrally monitor and regulate software deployments. By ensuring that only approved and current software is installed on endpoints, this centralized control helps to reduce the risks related to unapproved or out-of-date programs. Furthermore, features that control the execution of particular apps, such as application whitelisting and blacklisting, give an additional layer of security.
4) Compliance and Policy Enforcement:
It is imperative that security rules and compliance requirements be followed at all times. ITMS helps businesses enforce security rules by centralizing policy administration and guaranteeing uniform compliance throughout the IT infrastructure. Ensuring compliance with industry requirements and internal security policies is made easier for organizations with regular reporting capabilities.
5) Incident Response and Automation:
An automated, quick response is crucial in the event of a security problem. Organizations can quickly identify, evaluate, and address security events thanks to ITMS's automated incident response protocols. Features for logging and monitoring offer insights in real-time, improving the organization's total incident response capabilities. OnePane helps you in faster incident management by consolidating alerts and resource info from multiple tools to create incidents later which are mapped to the right resources, helping teams accelerate incident resolution.
6) Continuous Improvement and Adaptability:
A dynamic IT security plan needs to be flexible and always improving. This is made possible by ITMS, which makes it easier to conduct routine security audits, evaluations, and modifications in response to shifting organizational dynamics and threats. The usage of an iterative strategy guarantees the sustained effectiveness and resilience of security measures.
7) Endpoint Security Enforcement:
An essential component of any IT security plan is endpoint security. Real-time protection against harmful software is provided by ITMS, which combines antivirus and anti-malware software. Endpoint encryption ensures data integrity and reduces the possibility of data breaches by adding another layer of protection to sensitive data kept on devices.
Implementation of ITMS in the company :
Let's see how the adoption of ITMS positively affects the company. For example, Ben Corporation is a medium-sized company with a diverse IT infrastructure with various devices, networks, and software applications connecting different departments But currently, the major challenges for Ben Corporation is efficient management of IT assets, providing organization-wide security, and timely incident response.
To solve this problem, Ben Corporation chooses to put in place an IT Management Suite (ITMS) solution in order to deal with these issues. They select a full suite of modules for software deployment, asset management, patch management, security, and reporting. After this, Ben Corp can maintain an accurate inventory of all IT assets, including computers, servers and software licenses which helps in tracking new software installations within the organizations By conducting routine scans, the ITMS finds vulnerabilities and applies patches to minimize potential risks and shrink the attack surface. Apart from detecting the vulnerabilities it also responds to potential threats in real-time. The best part of the ITMS is it generates reports which help IT teams in making data-driven decisions.
Ben Corporation uses ITMS to improve security, expedite IT management procedures, and guarantee the smooth operation of its IT infrastructure. Better control, fewer vulnerabilities, and a proactive approach to IT administration are the outcomes of the deployment.
Conclusion:
Organizations may strengthen their security measures against emerging cyber threats with the help of ITMS, which offers centralized control and automated operations. The above example of Ben Corporation serves as an illustration of practical benefits. increased security, improved operational efficiency, and scalability for future expansion