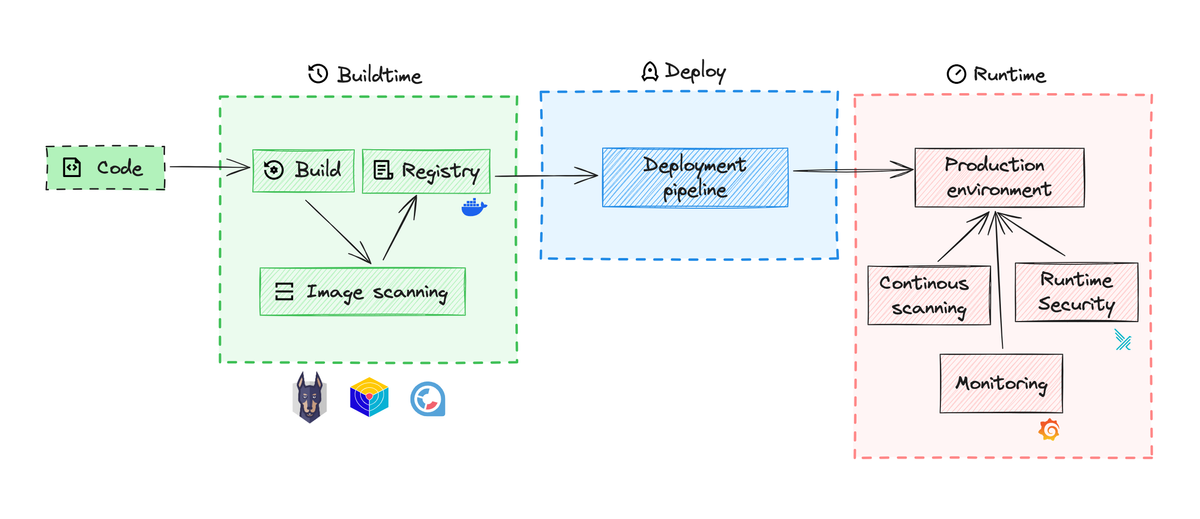
In the world of DevOps, it's all about speed and efficiency. That's why containers have become so popular. They're lightweight, scalable, and portable, making it easy to deploy applications quickly. In the previous blog, we discussed how to build a secure container image and various industry standards. However, it's important to remember that containers also come with new security risks during runtime. But don't worry, there are specialized measures you can take to ensure the security of your containers.
Container runtime security refers to the proactive controls and measures employed to safeguard a containerized application during its runtime stage. When discussing container runtime security, we're taking precautions to keep your containerized application safe while running.
Kubernetes facilitates the deployment, scaling, and management of containerized applications.
There are some best practices that we can follow to attain container runtime security.
1.Container Isolation:
Ensure proper isolation between containers by leveraging container runtime features such as namespaces and control groups (cgroups).
- Namespaces: Container runtimes use namespaces to provide isolation for processes, networks, mount points, and other resources.
docker run --rm --name mycontainer --pid=host --network=bridge --memory=512m myimage
for instance, this command starts a container namedmycontainerwith its own PID namespace, using the bridge network mode, and limiting its memory usage to 512 megabytes - Control Groups (cgroups): By using cgroups, you can prevent containers from monopolizing system resources and ensure fair resource allocation across multiple containers.
--memory,--cpu,--blkio,--network: commands in docker Sets resource limits and constraints using cgroups.
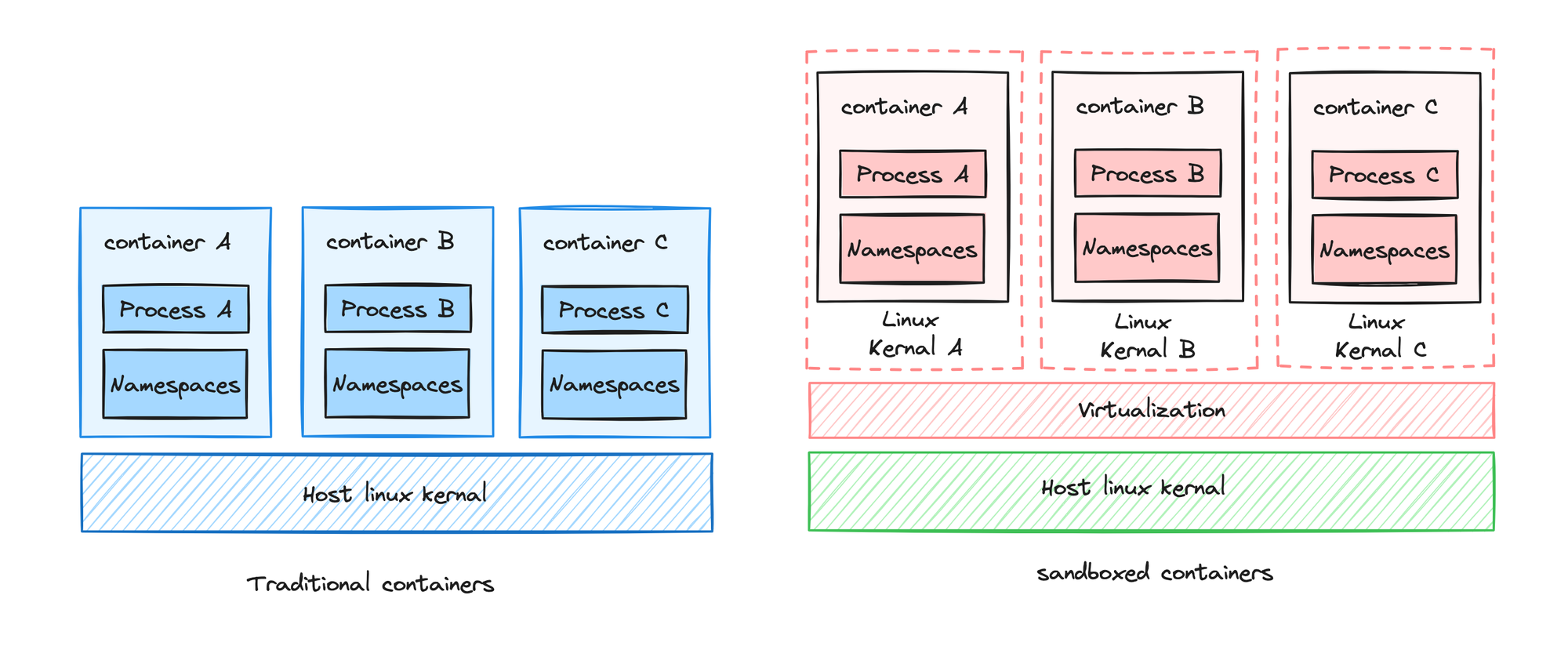
2.Runtime Sandboxing:
Employ runtime sandboxing techniques like gVisor or Kata Containers to add a layer of isolation and security around containerized workloads. Sandboxing isolates container processes from the underlying host system, and it also helps boost container security by isolating resources, protecting at the kernel level, reducing attack surface, enforcing policies, allowing for dynamic configuration, and enabling auditing and monitoring.
3.Least Privilege Principle:
Follow the principle of least privilege by restricting containers' permissions to only what is necessary for their intended functionality.
4.Runtime Monitoring:
Implement comprehensive monitoring solutions to continuously monitor container activities and detect any suspicious behavior or security incidents in real-time, like Falco
5.Vulnerability Scanning and Patch Management:
Regularly scan container images and runtime environments for known vulnerabilities using vulnerability scanning tools like Clair, Trivy, or Anchore.
- Access Control and Authentication:
Enforce strong access control measures by implementing role-based access control (RBAC) and multi-factor authentication (MFA) to restrict unauthorized access to containers and associated resources.
Several tools are available for implementing container runtime security, each with strengths and features. Let's explore some of these in this blog.
Falco
Falco is a runtime security tool that was created by Sysdig. It is now an incubating CNCF open-source project.
Falco has a rich set of security rules specifically built for Kubernetes, Linux, and cloud-native. At its core, it is a kernel monitoring and detection agent that observes events, such as syscalls, based on custom rules. Falco can enhance these events by integrating metadata from the container runtime and Kubernetes. If a rule is violated in a system, Falco will send an alert notifying the user of the violation and its severity or you can send it into SIEM for analysis.
For instance, we can try running Falco on a Kubernetes cluster, and let's try running some commands on the shell.
Add the Falco Helm repository
helm repo add falcosecurity https://falcosecurity.github.io/charts
helm repo updateInstall Falco in Kubernetes
helm install falco -n falco --set driver.kind=ebpf --set tty=true falcosecurity/falcoEnsure Falco pods are running
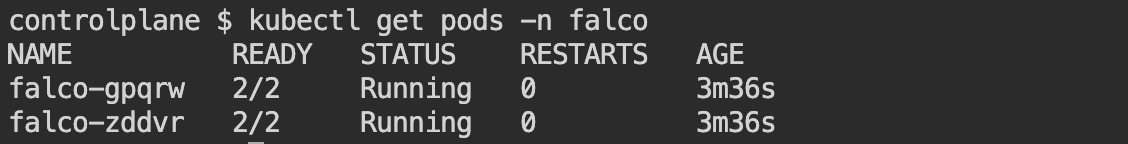
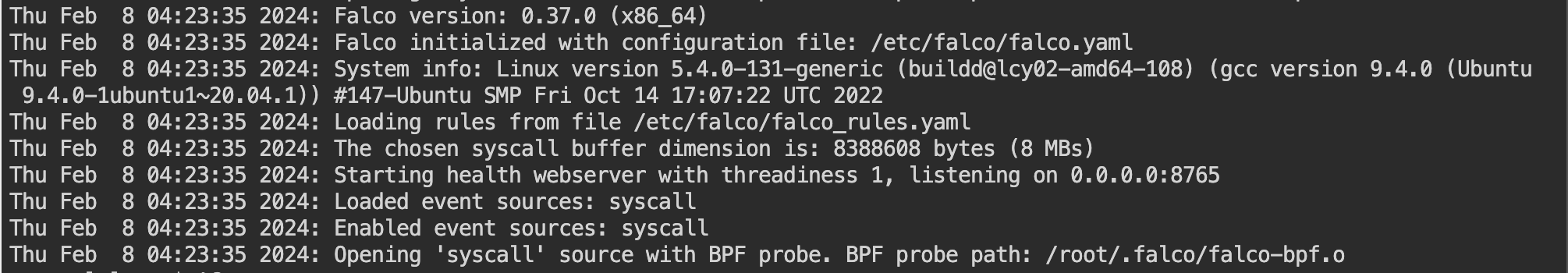
Verify Falco's running status by checking logs
kubectl logs -l app.kubernetes.io/name=falco -n falco -c falcoIf there is no problem you should see logs like this
To simulate syscalls let's spin an alpine container
kubectl run alpine --image alpine -- sh -c "sleep infinity"Shell into the running container and run the PWD command.
kubectl exec -it alpine -- sh -c "pwd"By default, Falco writes all events into stdout, so you can check logs for Falco pods
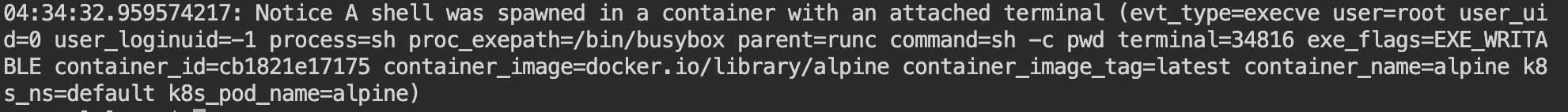
As you can see Falco was able to detect a shell spawn from one of the containers inside Kubernetes. This comes under the default rules available in Falco and there are many useful rules available in it. Falco also supports forwarding your events into tools like Slack, so that you can proactively monitor your environment.
To enhance the security of your containerized applications, it's important to follow the best practices for runtime security throughout the deployment lifecycle. This means implementing security measures at every step to ensure your applications are secure. By doing so, you can significantly improve the security posture of your containerized applications.